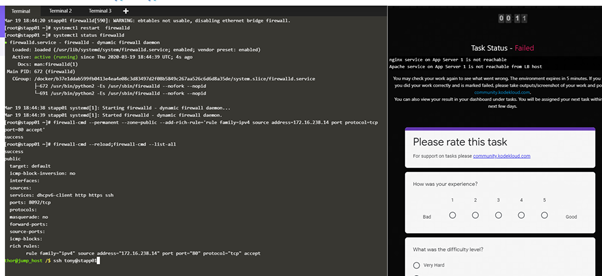
Hello Support ,
Linux Firewalld Setup task failed
Following steps followed
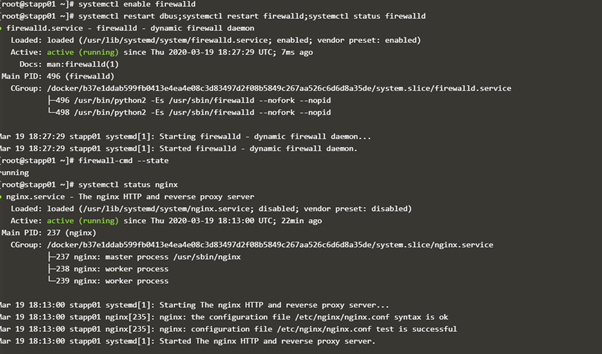
systemctl restart dbus;systemctl restart firewalld;systemctl status firewalld
firewall-cmd --state
systemctl status nginx
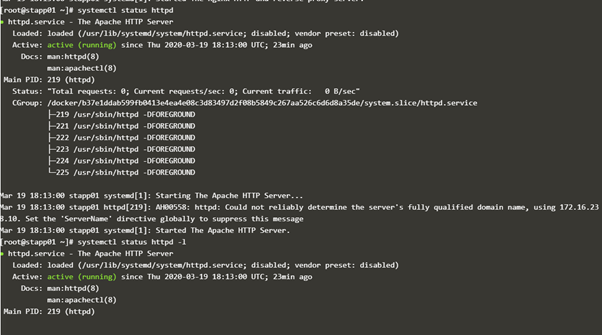
systemctl status httpd
modprobe iptable_filter
systemctl restart firewalld;systemctl status firewall
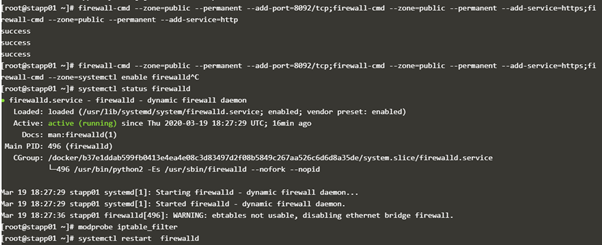
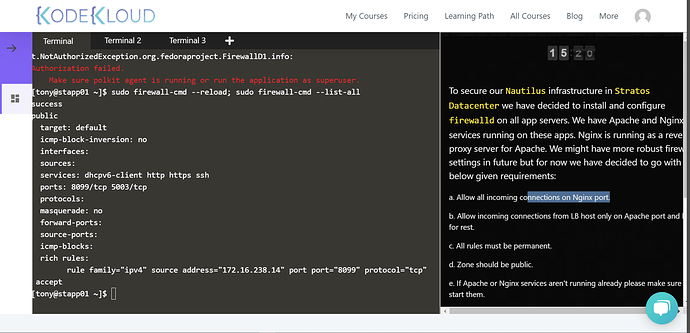
firewall-cmd --zone=public --permanent --add-port=8092/tcp;firewall-cmd --zone=public --permanent --add-service=https;firewall-cmd --zone=public --permanent --add-service=http
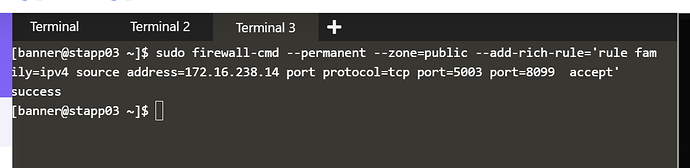
firewall-cmd --permanent --zone=public --add-rich-rule=‘rule family=ipv4 source address=172.16.238.14 port protocol=tcp port=80 accept’
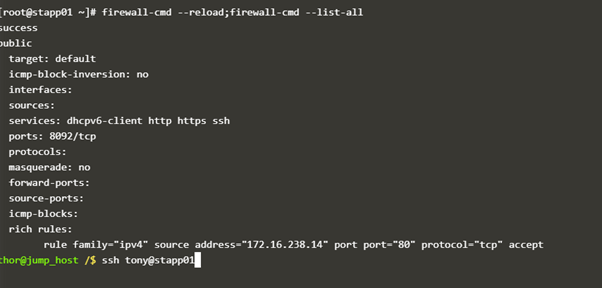
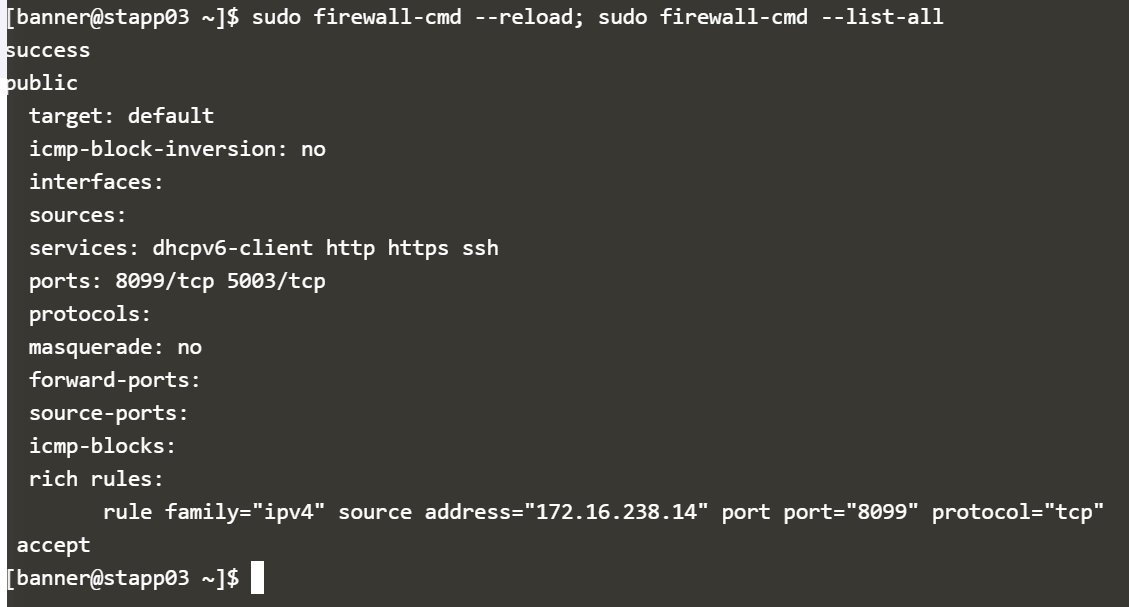
firewall-cmd --reload;firewall-cmd --list-all
Hi,
First of all, did you verify that actual port of httpd, because in general it is changed to another port (for example 6400 or 8083, …) and not 80, i think you supposed that the default one which is the 80 is used but it may be another.
Second did you change the rules on the 3 app servers ??? as is see you mentionned only the first server, how about the second and the third app server ?
Hi,
I have followed the same step for all 3 app servers.
1 Like
In rich rules, the apache port you mentioned is wrong. That would be the reason for the task failure.
I know this is an old post, but for someone who comes across this post and wants to confirm the ports do the following below:
find out which port is apache runing on by using ss -ntlpu and checking the .conf file if that’s the port its listening on.
cat /etc/httpd/conf/httpd.conf |grep Listen
1 Like
Hi Rajesh,
were you able to complete this task?
as part of this task. I followed these steps.
a. Install firewalld on 3 app servers.
systemctl service start, enable, status.
check nginx and httpd service on all three servers.
c. All rules must be permanent.
d. Zone should be public.
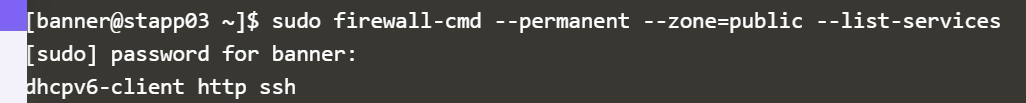
sudo firewall-cmd --permanent --zone=public --list-services
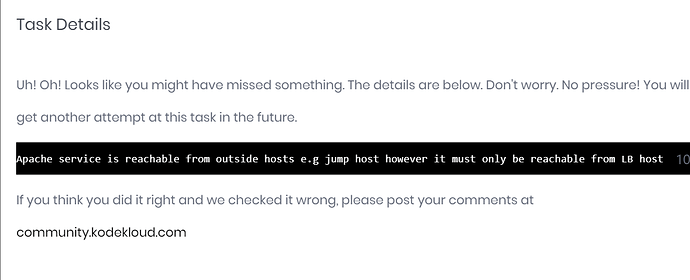
b. Allow incoming connections from LB host only on Apache port and block for rest.
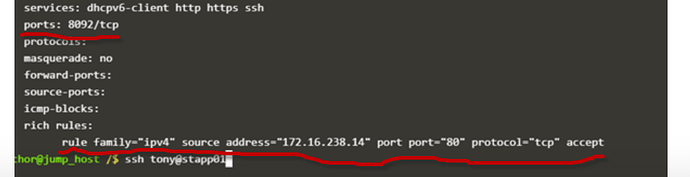
The below screenshot is from your results. what was supposed to be done in rich rules and ports section?
Please check and advise.
Hey,
Rich rules are an additional feature of firewalld that allows you to modify the rules a bit further.
it lets you whitelist IP or IP range . Reroute incoming traffic from on port and forward it another port. limit the incoming request. logging incoming request. you can find more info using man firewalld.richlanguage.
As you can see in the screenshot, that incoming connection from the source host (172.16.xxx.xxx) on such port is accepted .
Please view the following links below to get a better understanding
Your answer to your question is in the "task details ". Read carefully and also look at the last screenshot you have attached
Hi Swaroop,
Allow incoming connections from LB host only on Apache port and block for rest. This is where it went wrong.
@Tej-Singh-Rana
Hi Tej,
If I was hitting the deadline, assuming one of you will reply back soon. so I was copying all of you.
Thanks
Swaroop
Hi, Swaroop
okay. I will give your question's response as soon as possible.