Gv Avinash:
I have a general question on Network Policies. Is there a way to define exceptions for network policy. For example, how do i write a network policy that allows all ingress traffic on pod a with label “role: db” except from pod with label “role: client”. So basically how to restrict traffic from a particular pod.
unnivkn:
Gv Avinash:
thanks @unnivkn .so would this be correct apiVersion: http://networking.k8s.io/v1|networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: test-network-policy
namespace: default
spec:
podSelector:
matchLabels:
role: db
policyTypes:
- Ingress
ingress: - from:
- podSelector:
except:
matchLabels:
role: client
- podSelector:
unnivkn:
just try in our lab… I believe it will work… I didn’t tested this scenario…
Gv Avinash:
sure.thanks
Gv Avinash:
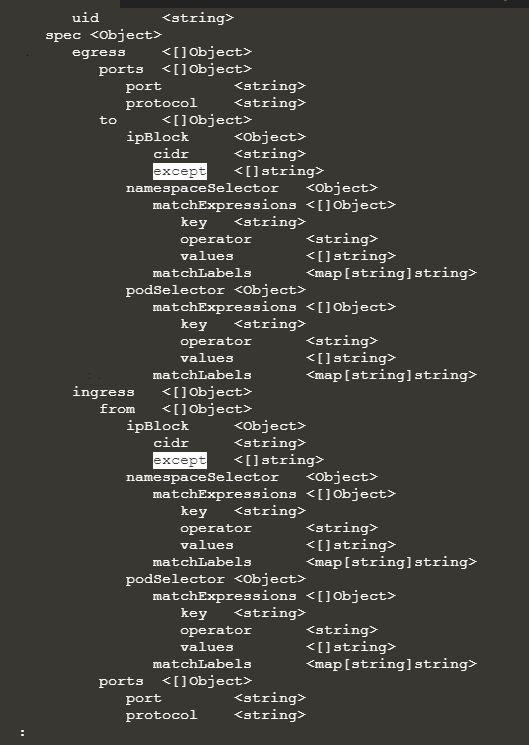
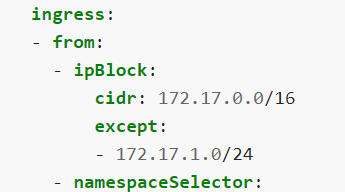
looks like except is only supported for ip addresses. applying above code allowed traffic from client pod. Explaining netpol also doesn’t show the except option for pods and namespaces
Sangeetha Radhakrishnan:
can you try using matchExperssions like below
podSelector:
matchExpressions:
- key: role
operator: NotIn
values: [client]
https://kubernetes.io/docs/concepts/overview/working-with-objects/labels/#resources-that-support-set-based-requirements
Deepak Ladwa:
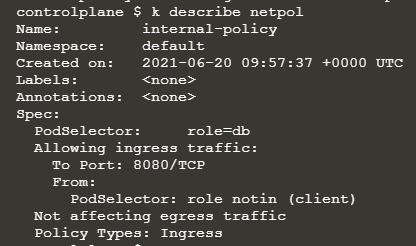
@Sangeetha Radhakrishnan So, this means - any pods in default namespace with label key “role” having a value which is not equal to “client” will be allowed to connect to the selector pod
unnivkn:
Pod with label role=db is allowing :
All other pods having label other than role=client
Deepak Ladwa:
Yeah.