kunal kapoor:
Hi there,
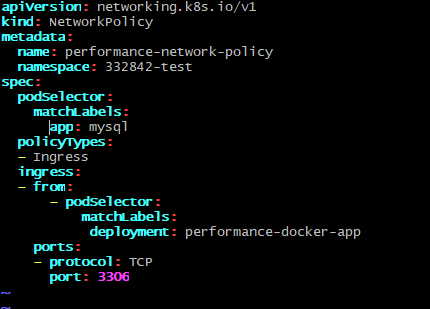
I have created a simple network policy that allows ingress to a MySQL Pod on port 3306 only from the application pod. I can see that the selectors for my podSelctors clause match for both the app and the MySQL pod.
I tried to test this policy by doing a curl from another pod to the mysql pod expecting the ingress to be restricted but rather the curl executed successfully and was able to connect to the MySQL pod.
Can someone please help and point it if I am missing something here?
Here’s the network policy yaml
Tej_Singh_Rana:
Hello, @kunal kapoor
which network plugin you have deployed in your cluster?
kunal kapoor:
@Tej_Singh_Rana I don’t have access to the kube-system namespace , so I can’t be sure about that.
Is there any other way to verify the network plugin and if it is enabled for the cluster.
It is a company wide cluster so I am sure the network plugins should have been enabled but could be restricted t specific namespaces
Tej_Singh_Rana:
Please ask them who have access.
Tej_Singh_Rana:
Flannel doesn’t support network policy. Calico, weave does.
kunal kapoor:
Thanks. Just a side note , there are other net work policies like allow-all-internal, deny-by-default etc also applied to this namespace. I am assuming that should not be an issue because once a specific policy is applied to a particular pod then those policies are overriden
