Gokboru:
Hi,
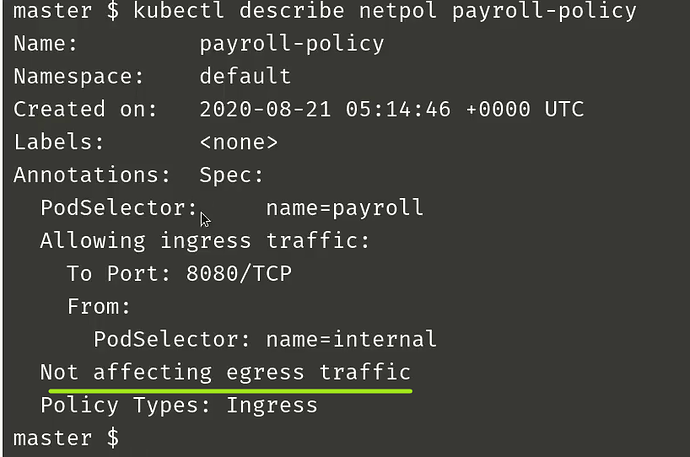
I have question about the coding exercise related to NetworkPolicy in CKA course. The question is about the highlighted line “Not effecting egress traffic” in below snapshot.
Does it mean that all Egress traffic is allowed? Or something else?
According to the lecture if we specify policy up to the level shown below (till role: db), all traffic in and out of POD will be blocked.
To allow specific traffic we have to specify Ingress or Egress and then only that traffic will be allowed. That is why if someone can clarify the statement “Not effecting egress traffic” in that context will be great.
apiVersion: http://networking.k8s.io/v1|networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: db-policy
spec:
podSelector:
matchLabels:
role: db
Mohamed Ayman:
That’s means that network policies do not conflict; they are additive. If any policy or policies select a pod, the pod is restricted to what is allowed by the union of those policies’ ingress/egress rules. Thus, order of evaluation does not affect the policy result
https://kubernetes.io/docs/concepts/services-networking/network-policies/|https://kubernetes.io/docs/concepts/services-networking/network-policies/
Gokboru:
@Mohamed Ayman In this specific case would it be correct to say that all Egress traffic is allowed?
Mohamed Ayman:
All allow is no longer valid when a pod is bound to a network policy
NetworkPolicy can be bind to a POD only because It control traffic flow at the IP address level
Gokboru:
It implies all egress traffic is blocked for this case where ingress is already applied.
Fernando Jordan Silva:
No, in your case there is no egress policy applied so all traffic is allowed. Networkpolicies works in a deny-allow mode, that means that if you set a policy, all traffic is denied except for the rules that you add in the policy.
As you have not added the “type: egress” in your policy, this policy does not affect to your egress traffic.
For example: Deny-all policy (deny all ingress & egress trafic)
apiVersion: <http://networking.k8s.io/v1|networking.k8s.io/v1>
kind: NetworkPolicy
metadata:
name: deny-all
namespace: default
spec:
podSelector: {}
policyTypes:
- Ingress
- Egress
Other example: denay all egress but not for pods with label “project: myproject”
apiVersion: <http://networking.k8s.io/v1|networking.k8s.io/v1>
kind: NetworkPolicy
metadata:
name: test-policy
namespace: default
spec:
podSelector: {}
policyTypes:
- Ingress
- Egress
egress:
- to:
- namespaceSelector:
matchLabels:
project: myproject
Gokboru:
Perfect @Fernando Jordan Silva. Now it is all clear. Thank you so much for your answer.