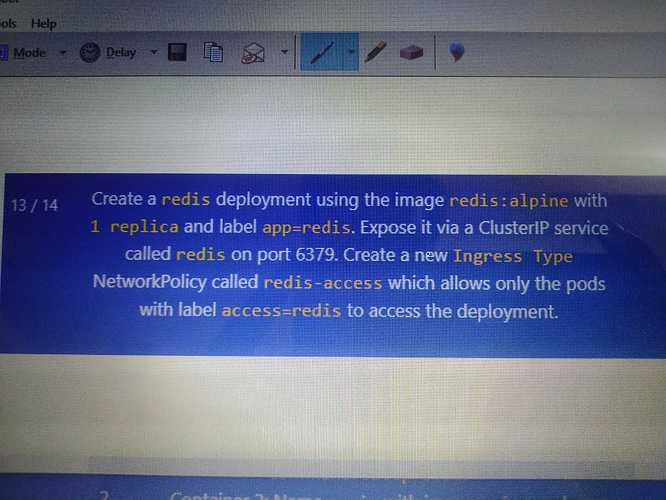
Abhijit Shinde:
Hi frnds, i think in this question(ckad mock1), while creating ingress network policy the labels should be used as app=redis instead of access=redis(maintained in question) to access the deployment, as deployment has the label app=redis. pls correct me if i amwrong. need to clear this doubt.
Abhimanyu Kolakotla:
I believe the question says you need to provide ingress to pods with label access=redis to the pod having label app=redis
Abhimanyu Kolakotla:
So its ingress network from app=redis to access=redis
Mohamed Ayman:
You should add the label access-redis to match it in netpolicy after creating the deployment by following those steps
1- $ kubectl create deployment redis --image=redis:alpine
2- add the required label by running $ kubectl expose deployment redis --port-6379 --labels=app=redis
3- Create the network policy using $ vi <newfilename.yaml> as below apiVersion: http://networking.k8s.io/v1|networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: redis-access
namespace: default
spec:
podSelector:
matchLabels:
app: redis
policyTypes:
- Ingress
ingress: - from:
- podSelector:
matchLabels:
access: redis
4- create it using $ kubectl apply -f <newfilename.yaml>
- podSelector: